In this post, I will provide the steps for configuring object access auditing so that you can detect an attacker extracting password hashes from the Windows registry.
These auditing settings can be applied to endpoints across your environment via Group Policy but in this example, I will be applying the settings to a single computer.
Configure Registry Auditing to Detect Access to Registry Hives/Keys
Under the “Local Computer Policy” settings (Group Policy if applying settings from a domain controller, turn on “Audit object access” for successful and failed access events.
In regedit.exe, apply the configuration below to monitor for successful and failed read attempts to the following root keys and subkeys:
Cached Domain Credentials:
HKLM\Security (This key only)
HKLM\Security\Cache (This key and subkeys)
HKLM\System (This key only)
LSA Secrets
HKLM\Security (This key only)
HKLM\Security\Policy\Secrets (This key and subkeys)
HKLM\System (This key only)
Local password hashes
HKLM\Sam (This key only)
HKLM\System (This key only)
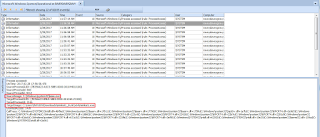
Detect Access Attempts to Registry Keys and Sub-Keys
You will see Event ID 4656 logged when password hashes are dumped from the registry using tools such as as Mimikatz, Pysecdump, Metasploit.
mimikatz # lsadump::cache
Detect Use of reg.exe to Save Registry Hives
You will also see Event ID 4656 when reg.exe is used to save the HKLM\Security, System, or Sam registry hives.
reg.exe SAVE HKLM\sam sam_backup.hiv
reg.exe SAVE HKLM\security
security_backup.hiv
reg.exe SAVE HKLM\system
system_backup.hiv
I hope you found this information useful. Please feel free to contact me with any questions or share any other techniques you have for detecting password dumping activity.