Mimikatz (https://github.com/gentilkiwi/mimikatz) is a popular tool used by adversaries (and Red Teamers) to dump passwords from memory. Password dumping from memory is more difficult to detect than dumping passwords from the Windows registry.
In this post, I will provide the steps for how to detect passwords being dumped from memory by configuring Sysmon v6. You can then filter the logs before forwarding the appropriate sysmon events to your SIEM.
Install and Configure Sysmon v6
Download Sysmon v6: https://technet.microsoft.com/en-us/sysinternals/sysmon
Create a file named sysmon_config.xml and copy the configuration below into the file.
<Sysmon schemaversion="3.3">
<HashAlgorithms>SHA256</HashAlgorithms>
<EventFiltering>
<ProcessAccess default="include">
</ProcessAccess >
</EventFiltering>
</Sysmon>
Install Sysmon using the configuration file you created:
sysmon64.exe -i .\sysmon_config.xml
Validate that the configuration has been applied by dumping the current sysmon configuration:
sysmon64.exe -c
Dump Passwords From Memory Using Mimikatz
To test the Sysmon Process Access logging, dump your passwords from memory using Mimikatz.
PS C:\Users\fmfx009\Downloads\mimikatz_trunk\x64> .\mimikatz.exe
privilege::debug
sekurlsa::logonpasswords
Review Sysmon Event Logs for Mimikatz Usage
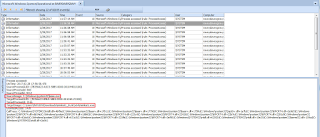
Access the Sysmon logs via the Event Viewer under Microsoft-Windows-Sysmon/Operational or use the filtering features of Event Log Explorer.
Apply a filter to view all events with Event ID 10, “Process accessed”.
You should see evidence of SourceImage: lsass.exe accessing TargetImage: mimikatz.exe. You should also see evidence of SourceImage: mimikatz.exe accessing TargetImage: lsass.exe
I will write some additional posts soon on how to detect other credential dumping tools on your endpoints.
Please feel free to contact me with any questions. If you have any other techniques for detecting password dumping activity, I would be happy to hear from you. I hope this information helps.
I experienced issues configuring Sysmon v6 to monitor Process Access and have reported a bug to Mark Russinovich; the current configuration output shows Process Access as disabled when it is actually enabled.





No comments:
Post a Comment