Cowrie is a medium interaction SSH and Telnet honeypot, which can log brute force attacks and an attacker's shell interaction.
Cowrie is an excellent project developed by Michel Oosterhof.
This post provides instructions on how to configure a Cowrie SSH honeypot on an Ubuntu 16.04 system. I recommend that you configure Cowrie on a cloud server instance rather than a host on your home network.
I will publish another post soon to show how to visualize the attacker's activity in Splunk.
Change the Port You Will Use to Administer the Server
Cowrie will be listening for SSH connections on port 22. You'll want to configure the SSH service to listen on a different port for you to connect to and administer the server.
sudo vi /etc/ssh/sshd_config
Under "# What ports, IPs and protocols we listen for", change the port number to 3393 or your preferred port number.
Write your changes and quit vi.
Ctrl + C
:wq
Restart the SSH service.
service ssh restart
By running the command below, you can see that the server is now listening for connections on port 3393.
netstat -tan
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp0 0 0.0.0.0:3393 0.0.0.0:* LISTEN
Install and Configure Cowrie
Download updated package lists.
sudo apt-get update
Install Cowrie's dependencies.
sudo apt-get install python2.7 git virtualenv libmpfr-dev libssl-dev libmpc-dev libffi-dev build-essential libpython-dev python-pip
Add a new user named, cowrie.
sudo adduser --disabled-password cowrie
Switch to the new user, cowrie
sudo su - cowrie
Navigate to the home directory of user, cowrie, and clone the cowrie git repository.
git clone https://github.com/micheloosterhof/cowrie.git
Create a new virtual environment for cowrie.
cd cowrie
virtualenv cowrie-env
Activate the virtual environment.
source cowrie-env/bin/activate
The terminal will display "(cowrie-env)" before the username, cowrie.
Install pycrypto, Crypto and other requirements.
pip install pycrypto Crypto
(cowrie-env)$ pip install -r requirements.txt
Generate a DSA key for the cowrie instance.
cd data
ssh-keygen -t dsa -b 1024 -f ssh_host_dsa_key
cd ..
export PYTHONPATH=/home/cowrie/cowrie
Additional Cowrie Configuration
Make a copy of the config file for your new cowrie instance.
cd /home/cowrie/cowrie/
cp cowrie.cfg.dist cowrie.cfg
vi ./cowrie.cfg
Set the hostname in the configuration file to a server name of your choice. E.g. "fileserver4"
Change the "Port to listen for incoming SSH connections" to port 22.
Write your changes and quit vi.
Ctrl + C
:wq
Enable authbind in cowrie's start.sh file.
sudo vi /home/cowrie/cowrie/start.sh
Change line 2 to read:
AUTHBIND_ENABLED=yes
sudo apt-get install authbind
sudo touch /etc/authbind/byport/22
sudo chown cowrie /etc/authbind/byport/22
sudo chmod 777 /etc/authbind/byport/22
Start Cowrie
Execute the following commands to start Cowrie.
sudo su cowrie
cd /home/cowrie/cowrie/
source cowrie-env/bin/activate
./start.sh
Verify cowrie is listening on port 22 by running the command below.
netstat -tan
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
Execute the following command to stop Cowrie.
./stop.sh
How to Stop and Start the SSH Service (Running on the Custom Port You Chose Earlier)
If your server is accessible via a console in your cloud provider's management console, you may want to disable the SSH service on your server and enable it only when you need to establish a SSH connection to administer it.
This will prevent SSH brute force attacks against the listening service.
Execute the following command to stop the SSH service.
sudo /etc/init.d/ssh stop
Validate that the server is no longer listening on the custom SSH port. You should see that Cowrie is still listening on port 22.
netstat -tan
Execute the following command to start the SSH service.
sudo /etc/init.d/ssh start
Test Connectivity to the Cowrie Honeypot
Connect to your server on port 22, enter any password and you will be authenticated successfully.
Execute some commands for Cowrie to log.
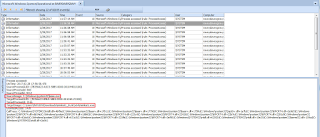
Review the Cowrie Log File
Connect to your server (not the Cowrie instance) and review the log file.
cat /home/cowrie/cowrie/log/cowrie.log | less
The attacker's IP address will be shown in the red areas in the image below.
I will be writing a post soon on how to visualize the attacks against your honeypot using Splunk.